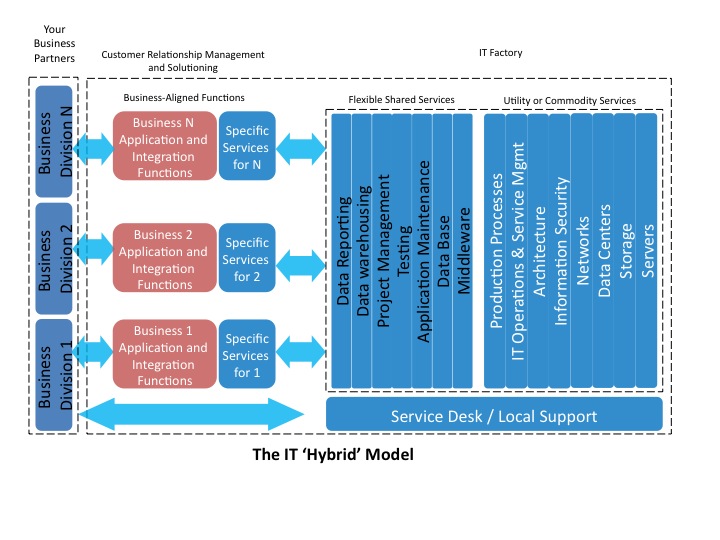
There is a ‘tipping point’ within Call Centre mechanics which means that the rate of deterioration will become exponential – i.e., the gentle gradient of deterioration does not last long before service falls over the cliff edge (i.e. wait times in seconds, quickly become minutes and then tens of minutes – even hours). Calls are abandoned by customers, with call backs adding further volume. Agents become overworked and stressed due to the tone of the calls, their efficiency reduces and attrition goes up, exacerbating any supply shortage. These dynamics also work in reverse and so what can seem to be an insurmountable problem can in fact be rapidly returned to stability if managed appropriately.
Common supply side issues include:
- Organisations increasingly use headcount caps and quotas to control their cost base. As the quota filters through the organisation, there can be a tendency to retain ‘higher end’ roles, which means the Service Desk comes under particular scrutiny and challenge. A reduction in the supply of labour (without equivalent changes in demand) can very quickly lead to significant service deterioration.
- Similarly, Service Desk tends to be a function in which organisations have an uplifted appetite to make organisational changes to outsource and offshore (and similarly insource and onshore as the cycle runs). The wholesale replacement of the Service Desk workforce is a fairly common scenario within the industry and is frequently the root cause of acute service issues in the run up to change (as attrition without replacement bites) and during and post change (as a new workforce struggles to support their new customer base).
- Any issue / initiative that either reduces the availability of agents to handle live calls or leads to a significant increase in the transaction time to do so can very quickly have a catastrophic impact on service. For example; the implementation of a new Service Management toolset is likely to elongate call duration in the short to medium term, a call centre with a high attrition rate will constantly lose agents just as they start to perform – to be replaced by a trainee performing at a sub optimal level and a call centre operating at too high an occupancy level will quickly burn out staff and have an increasing level of absenteeism.
Demand side issues commonly include;
- Growth of the user base, generating an uplifted volume of contacts to the Service Desk.
- An increase in contacts per supported user, driven by increasing IT usage or deterioration of IT performance (this is frequently driven by Business or IT change activity delivered by Projects and Programmes – such as the deployment of a new application to the workforce).
Irrespective of the root cause of the failure, service remediation needs to be a concerted effort combining strong analysis with disciplined planning and focused execution. Identifying that there is an issue and responding appropriately in a timely manner should happen automatically if you are already operating with maturity from fact based metrics that have a healthy mix of lead and lag indicators. If the organisation is less mature in its use of metrics (and particularly lead indicators) then the ‘crisis’ is not likely to be noticed (or at least taken seriously by senior leadership) until after the Service Desk hits the tipping point and service is deteriorating at an alarming pace, generating severe customer dissatisfaction (i.e. until it is too late).
Remediating a failing Service Desk requires multiple and varied actions dependent upon the root cause of the issues. The approach to identifying and rectifying those root causes can be managed effectively by following a logical framework.
Step 1 – Stabilize
If service has tumbled over the tipping point and is deteriorating rapidly, there is going to be little sponsorship for an extended analysis and planning exercise. Results – or at least avoiding further deterioration of performance – will be expected immediately. Your first priority is to create the space to put together a meaningful recovery plan.
Do everything that you can do to boost the supply side in the short term (overtime / shift amendments / cessation of any non-time critical, non-customer contact work by your agents, boost the number of agents by diverting resources to customer service roles from other positions etc, bring in temporary resources, etc). This will not fix the issue and is not a sustainable containment strategy; it will however create the window of opportunity you require and give a much needed boost to stakeholder confidence that the ‘freefall’ may be over. By itself, it will reduce the cycle of abandons and call backs that create additional work for the team.
Similar attention should be paid to any demand side actions that can be deployed quickly, it is less likely however that you can act immediately on the demand side, but there are steps that can be taken quickly. If there are recent system or application rollouts that are generating questions and calls, it may be worthwhile to send out a FAQ or Quick Tips to help employees understand what to do without calling the service desk. Or any self help initiatives already in the pipeline could be accelerated to remove some calls. While these actions are more likely to form elements of your strategic recovery plan, the may provide some level of relief.
Step 2 – Undertake the Analysis
Your leadership group and analysts need to undertake the analysis to understand why service has deteriorated. What has gone wrong, when, where and why? If your desk has been performing well (or even adequately) for some time, remember that a recent ‘change’ in either the demand or supply side is likely to be the root cause.
If the desk has been underperforming for a significant period, there are likely to be more systemic causes of the failure and so a full strategic review of your operations is required. Reading the full set of Service Desk Best Practices published within Recipes for IT will provide guidance on the areas of focus required.
After understanding your call volumes and their trends (everything from call time to why customers are calling) you should be able to identify some of the root causes. Are there new issues that are now in the top 10 call reasons? Are your call times elongated? Have call volumes or peaks increased? For each shift in metrics, analyze for the following:
- determine if the root cause for a customer call is due to:
- system issues or changes
- user training or understanding
- lack of viable self-service channel
- identify if increases in calls are due to:
- underlying user volume increases or growth
- new user technologies or systems
- major rollouts or releases that are problematic
- or if service is suffering due to:
- lack of resources or mismatched resource levels and call volumes
- inadequate training of service desk personnel
- new or ineffective toolsets that elongate service time
- inefficient procedures or poor engagement
- high attrition or loss of personnel
If you do not have adequate metrics to support the analysis, then you will need to establish basic metrics collection as the first, fundamental step.
Step 3 – Construct the Recovery Plan
Constructing the recovery plan needs to be genuinely solution-oriented and outcome focused. The objective of the plan is not usually to resolve the source of the ‘shock’ to return us back to the old equilibrium (e.g. we aren’t likely to want to back out the new Service Management toolset that we have just implemented – we will want to build forward). The objective of the plan is to detail the actions required to resolve the issues identified as well as build a solid foundation to allow us to move back to a steady state operation, delivering with quality and consistency to our SLA.
A good recovery plan will be clear about what actions are to be undertaken, by who, when, to achieve which specific deliverable and with specific measures and metrics tracking progress to achievement of the overall outcome.
The plan needs to focus on prioritising actions that can make a positive impact of scale and of pace commensurate to the scale of the service issues being experienced. Many and multiple actions on a service recovery plan creates a false sense of comfort for those involved in the crisis and will almost certainly hinder genuine service improvement. Targeted action is required and this needs discipline and skill from the plan owner to ensure that benefits will be realised, will be relevant to the problem statement and that our actions in aggregate will move bottom line performance to where we need it to be.
We recommend a recovery plan that has the following elements:
a. Maintain an interim staffing boost to stabilize the service desk until other work is completed
b. If clear problem causes are identified (poorly rolled out systems, ongoing defective systems causing high volumes of calls) then ensure these areas are high priority for fixes on the next release or maintenance cycle.
c. Match resources to demand cycles based on current volumes and call handle times. Then forecast proper resource levels based on improvement initiatives and their completion dates.
d. If self service can address a significant volume of calls, these should also be a top priority for investment as this solution is also usually an overall cost save as well as service experience improvement (e.g. password resets).
e. Ensure your service desk staff can efficiently handle calls — proper training, tool adjustments, thoughtful goals, incentives and a productive environment.
f. Address staff recruiting as well as development, incentives, and training and career progression to ensure you will have an engaged and well-trained staff to deliver exceptional service
g. Review your IVR and call centre technology setup and look to optimize menus, self-service, and call back options. Specialize resources into pools as appropriate to improve efficiency.
h. Define strategic service goals and SLAs along with initiatives to achieve them (e.g., additional or different sites, knowledge management tools, revamp of problem systems, etc).
Step 4 – Execute the Recovery Plan
Ensure that the plan is owned by an individual with the gravitas, influence, experience and focus to manage it through with real pace and drive. Ideally, the individual should not own actions within the plan itself (as this undermines their ability to hold everyone fully to account and removes their impartiality when inevitable conflicting priorities arise).
The plan can (and should) be meaningfully tuned as you progress with delivery. It should not however be a constant exercise in planning and re-planning and particular focus needs to be applied to ensure that commitments (delivery to time, cost and quality) are met by all action owners.
Communicate the issue, the plan, progress & improvement achieved to date and upcoming actions from your recovery plan to stakeholders. Ensure that stakeholder management is a specific activity within your plan and that you pay particular attention to each stakeholder group as a constituency. The role of senior leaders in recovery situations should be to protect the operations team to enable it to focus on delivery through the management of senior clients and customers and to ensure that the required resources to remediate the issues are provided.
Step 5 – Take a Look Back
Once service has been remediated and stabilised there are a number of residual actions to undertake.
- As additional resources were utilised in the recovery effort (holidays restricted, time off in lieu accumulated, overtime paid etc…) there may well be negative service and / or financial implications of those decisions. It is important to quickly understand any such impacts and to manage them appropriately (e.g., review the holiday allocation process to ensure accumulated holidays can still be scheduled without a bottleneck, determine whether to grant time off in lieu for extra hours worked or to pay overtime, ensure that departments and functions who have been loaning staff to the front line receive support and resources to now clear their backlogs quickly etc.).
- Review the control processes and responsiveness of your Service Desk in the identification of the issue / issues and how this could be improved upon in the future (in particular the use of lead and lag performance metrics). The ‘root causes’ identified should be eliminated or carefully tracked to ensure that future occurrences can be identified and dealt with before they manifest as service impact to your customers.
- Ensure that the findings of your root cause analysis are communicated to and understood by your stakeholders. Be honest, be clear and be candid about what has happened, why and the measures that are now in place to prevent / mitigate any future such occurrences.
- Say Thank You as the milestones are completed. A number of people will have participated in the recovery effort, some very explicitly and others in a very low key manner (for example by absorbing extra workload from colleagues seconded to the front line). Recognising their contribution and taking the time to say Thank You will ensure that your team feel rewarded for their efforts and motivated to stand shoulder to shoulder in tackling future adverse events that impact customer service.
And with these efforts, you will have turned the ‘helpless desk’ into a positive key interface for your customers.
Best, Steve Wignall and Jim Ditmore